Cybersecurity Researcher Jeremiah Fowler uncovered a data leak of 149 million logins and passwords, and shared his findings with ExpressVPN. We are publishing his report to help the public stay informed and protected as part of our ongoing effort to highlight important security risks.
The publicly exposed database was not password-protected or encrypted. It contained 149,404,754 unique logins and passwords, totaling a massive 96 GB of raw credential data. In a limited sampling of the exposed documents, I saw thousands of files that included emails, usernames, passwords, and the URL links to the login or authorization for the accounts. This is not the first dataset of this kind I have discovered and it only highlights the global threat posed by credential-stealing malware. When data is collected, stolen, or harvested it must be stored somewhere and a cloud based repository is usually the best solution. This discovery also shows that even cybercriminals are not immune to data breaches. The database was publicly accessible, allowing anyone who discovered it to potentially access the credentials of millions of individuals.
The exposed records included usernames and passwords collected from victims around the world, spanning a wide range of commonly used online services and about any type of account imaginable. These ranged from social media platforms such as Facebook, Instagram, Tiktok and X (formerly Twitter), as well as dating sites or apps, and OnlyFans accounts indicating login paths of both creators and customers. I also saw a large number of streaming and entertainment accounts, including Netflix, HBOmax, DisneyPlus, Roblox, and more. Financial services accounts, crypto wallets or trading accounts, banking and credit card logins also appeared in the limited sample of records I reviewed.
One serious concern was the presence of credentials associated with .gov domains from numerous countries
[…]
The database had no associated ownership information so I reported it directly to the hosting provider via their online report abuse form. I received a reply several days later stating that they do not host the IP and it is a subsidiary that operates independently while still using the parent organization’s name. It took nearly a month and multiple attempts before action was finally taken and the hosting was suspended and millions of stolen login credentials were no longer accessible. The hosting provider would not disclose any additional information regarding who managed the database, it is not known if the database was used for criminal activity or if this information was gathered for legitimate research purposes or how or why the database was publicly exposed. It is not known how long the database was exposed before I discovered and reported it or others may have gained access to it. One disturbing fact is that the number of records increased from the time I discovered the database until it was restricted and no longer available.
Breakdown of Email Providers (estimated)
- 48M – Gmail
- 4M – Yahoo
- 1.5M – Outlook
- 900k – iCloud
- 1.4M – .edu
Other notable accounts included:
- 17M – FaceBook
- 6.5M – Instagram
- 780k – TikTok
- 3.4M – Netflix
- 100k – OnlyFans
- 420k – Binance
This screenshot shows the total count of records and size of the exposed infostealer database.
This image shows screenshots of accounts and credentials including Instagram, Google accounts, and OnlyFans.
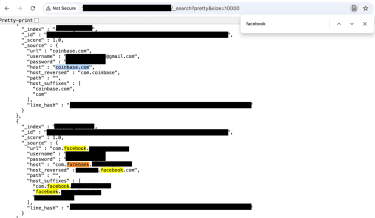
This image shows screenshots of accounts and credentials including Facebook, a government account from Brazil, and a WordPress administrative login.
This screenshot shows how the index was searchable using nothing more than a web browser.
The database appeared to store keylogging and “infostealer” malware,
[…]

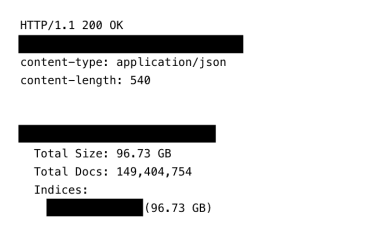 This screenshot shows the total count of records and size of the exposed infostealer database.
This screenshot shows the total count of records and size of the exposed infostealer database.