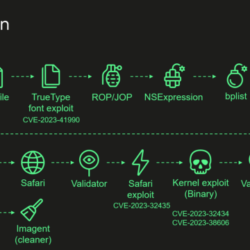
Apple’s ‘incredibly private’ Safari not so private in Europe, allows
Apple’s grudging accommodation of European antitrust rules by allowing third-party app stores on iPhones has left users of its Safari browser exposed to potential web activity tracking. Developers Talal Haj Bakry and Tommy Mysk looked into the way Apple implemented the installation process for third-party software marketplaces on iOS with Safari, and concluded Cupertino’s approach Read more about Apple’s ‘incredibly private’ Safari not so private in Europe, allows[…]