The Nefilim ransomware gang might not be the best known or most prolific online extortion crew but their penchant for attacking small numbers of $1bn+ turnover firms is paying off, according to some latest research.
The crew has made comparatively fewer headlines next to better-known criminals such as Darkside, perpetrators of the infamous US Colonial Pipeline attack, but analysis from security shop Trend Micro has shown the crooks appear to be going for big companies in the hope of extracting correspondingly big payouts.
“Of the 16 ransomware groups studied from March 2020 to January 2021, Conti, Doppelpaymer, Egregor and REvil led the way in terms of number of victims exposed – and Cl0p had the most stolen data hosted online at 5TB. However, with its ruthless focus on organizations posting more than $1bn in revenue, Nefilim extorted the highest median revenue,” said Trend Micro in a report released on Tuesday.
The information will be of little comfort to any of the western world’s growing number of ransomware victims, including the Irish Health Service Executive and the US Colonial Pipeline Company.
While those attacks were very high profile because of their wider impact on critical national infrastructure, other ransomware operators are still engaging in the good old-fashioned pursuit of money, and lots of it.
Nefilim is, according to Trend, a ransomware gang that was first observed in late 2019, with actual attacks being seen in March 2020 – just as the COVID-19 pandemic drove the entire world online and to remote working.
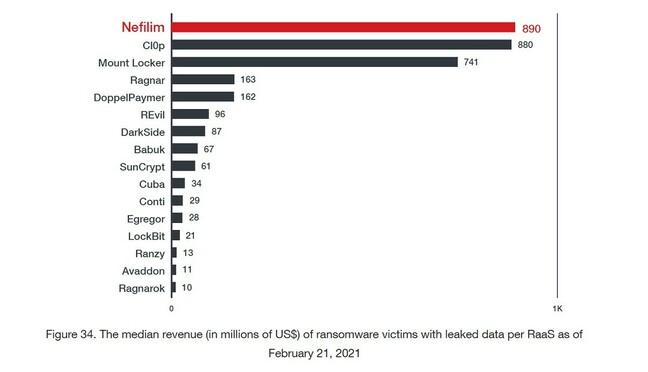
Trend Micro analysis of the Nefilim ransomware gang’s targets by revenue, based on identifiable leaked files. Click to enlarge
Despite targeting big businesses, Nefilim’s access methods were just the same as the ones constantly warned about by the infosec industry, said Trend Micro, explaining: “In the case of Nefilim ransomware attacks, our investigations uncovered the use of exposed RDP services and publicly available exploits to gain initial access — namely, a vulnerability in the Citrix Application Delivery Controller [CVE-2019-19781].”
Trend also referred to previous research from Digital Shadows on so-called initial access brokers, essential actors in the ransomware business chain who make the first break into a target’s networks before selling that illicit access to other criminal organisations.
“The price for access varies greatly — it can range from tens of dollars for a random victim asset, to several hundreds or even thousands of dollars for a categorized asset; access to the infrastructure of a large organization can cost five to six figures,” the report states.
Trend Micro research veep Bharat Mistry told The Register that ransomware gangs’ business models are just as developed as anything in the western IT market with different elements of attacks being carried out by different groups of criminals.
“There is a full partner model that goes with it. So you know, the ransomware as a service operators, they get around 20 to 30 per cent of the profit that comes out of it, and the rest of it goes to the partner. So you can see it’s margin-rich for the affiliates.”
Criminal gangs were also said to make “widespread use of legitimate tools such as AdFind, Cobalt Strike, Mimikatz, Process Hacker, PsExec, and MegaSync, to help ransomware attackers achieve their end goal while staying hidden.” Similarly, some in the infosec world call legitimate tools turned around and used against their owners LoLBins – living off the land binaries. In other words, tools such as PowerShell, which are in common use on corporate networks but can be harnessed as part of an attack on that same network.
While nothing about Nefilim’s operations are shockingly unique, that in itself ought to be a lesson for corporate infosec bods: it’s not the big scary vulns that let miscreants rampage through your employer’s network, it’s the ones everyone’s been warning about which you haven’t got round to patching for whatever reason.

Robin Edgar
Organisational Structures | Technology and Science | Military, IT and Lifestyle consultancy | Social, Broadcast & Cross Media | Flying aircraft
