Threat intel researchers have uncovered a phishing and malware campaign that targeted “a large European aerospace company” and which was run by the same North Koreans behind the hack of Sony Pictures.
While there are quite a few European aerospace firms, Slovakian infosec biz ESET was more concerned with the phishing ‘n’ malware campaign it detected on behalf of its unnamed client.
Branded “Operation Interception” by ESET, the researchers claimed the “highly targeted cyberattacks” were being spread by North Korean baddies Lazarus Group, who were behind the 2014 hack of Sony’s American entertainment business.
The threat group’s latest detected campaign involved targeting aerospace folk via LinkedIn, said the infoseccers. ESET researcher Jean-Ian Boutin explained: “In our case they were impersonating Collins Aerospace and General Dynamics (GD), two organisations in the same vertical as the targeted European organisations,”. He said the Norks were targeting people who worked in “sales, marketing, tech, general admin” roles.
Collins and GD are two of the bigger names in North American aerospace; among other things, Collins makes avionic instruments and software while GD has fingers in pies ranging from the F-16 fighter jet through Gulfstream corporate aircraft, US Navy submarines and armoured vehicles. As bait dangled before honest people hoping to take a major step forwards in an aerospace career, these two companies were tempting lures.
“The [job] offer seemed too good to be true,” said Boutin as he explained the Lazarus ruse to The Reg. “Maybe [the recipient’s] career could take off in a big way?”
Once into a target’s network the criminals would try to brute-force any Active Directory admin accounts they could find, as well as exfiltrate data by bundling it into a RAR archive and trying to upload it to a Dropbox account.
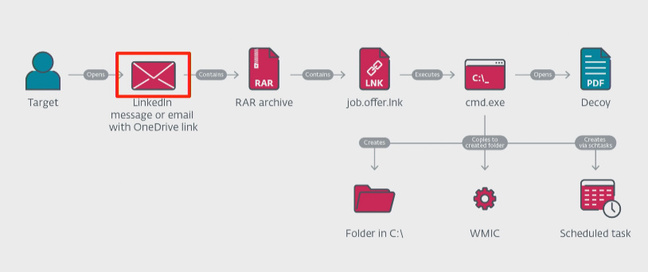
After the victim had been suitably reeled in, Lazarus would try to induce them to download a password-protected RAR archive “containing a LNK file.” Once clicked, that LNK file appeared to the victim to download a PDF containing job information. In the background, however, it also downloaded a malicious EXE that created a bunch of folders and set a Windows scheduled task to run a remote script every so often.

ESET illustration showing the Lazarus Group attack progression
The attackers were most insistent that the victim only respond to their job offer on a Windows machine running Internet Explorer. Once in, they resorted to PowerShell – taking advantage of the fact that “the logging of executed PowerShell commands is disabled by default,” although evidence was found that the Lazarus crew went through the connected domain to enumerate all Active Directory accounts before trying to brute-force their way into admin accounts.
To avoid Windows security features blocking their malware, Lazarus also signed their code using a certificate first issued to 16:20 Software LLC, an American firm said by ESET to have been incorporated in May 2010.
Among other clues linking the malware’s components back to North Korea, Boutin said his team had seen build timestamps “added by the compiler showing when the executable was compiled” which neatly cross-referenced with normal office hours for East Asia. Corroborating that were some “host fingerprinting” techniques which uncovered various digital fragments “similar to backdoors the Lazarus Group is known to use,” as Boutin put it.
What made the lure so sneaky was the fact it was targeting potential jobseekers looking to leave their current employer, a fact that Boutin speculated may have made some victims less likely to report it to their current employer’s cybersecurity teams.
Lazarus Group was last seen in public after it was caught sniffing around macOS with a trojan targeting users of Apple’s desktop operating system. ®

Robin Edgar
Organisational Structures | Technology and Science | Military, IT and Lifestyle consultancy | Social, Broadcast & Cross Media | Flying aircraft