You’re not just getting older. Song lyrics really are becoming simpler and more repetitive, according to a study published on Thursday.
Lyrics have also become angrier and more self-obsessed over the last 40 years, the study found, reinforcing the opinions of cranky aging music fans everywhere.
A team of European researchers analyzed the words in more than 12,000 English-language songs across the genres of rap, country, pop, R&B and rock from 1980 to 2020.
[…]
For the study in the journal Scientific Reports, the researchers looked at the emotions expressed in lyrics, how many different and complicated words were used, and how often they were repeated.
[…]
The results also confirmed previous research which had shown a decrease in positive, joyful lyrics over time and a rise in those that express anger, disgust or sadness.
Lyrics have also become much more self-obsessed, with words such as “me” or “mine” becoming much more popular.
‘Easier to memorize’
The number of repeated lines rose most in rap over the decades, Zangerle said—adding that it obviously had the most lines to begin with.
“Rap music has become more angry than the other genres,” she added.
The researchers also investigated which songs the fans of different genres looked up on the lyric website Genius.
Unlike other genres, rock fans most often looked up lyrics from older songs, rather than new ones.
Rock has tumbled down the charts in recent decades, and this could suggest fans are increasingly looking back to the genre’s heyday, rather than its present.
Another way that music has changed is that “the first 10-15 seconds are highly decisive for whether we skip the song or not,” Zangerle said.
Previous research has also suggested that people tend to listen to music more in the background these days, she added.
Put simply, songs with more choruses that repeat basic lyrics appear to be more popular.
“Lyrics should stick easier nowadays, simply because they are easier to memorize,” Zangerle said.
“This is also something that I experience when I listen to the radio.”
More information: Eva Zangerle, Song lyrics have become simpler and more repetitive over the last five decades, Scientific Reports (2024). DOI: 10.1038/s41598-024-55742-x. www.nature.com/articles/s41598-024-55742-x
Source: Song lyrics are getting simpler, more repetitive: Study













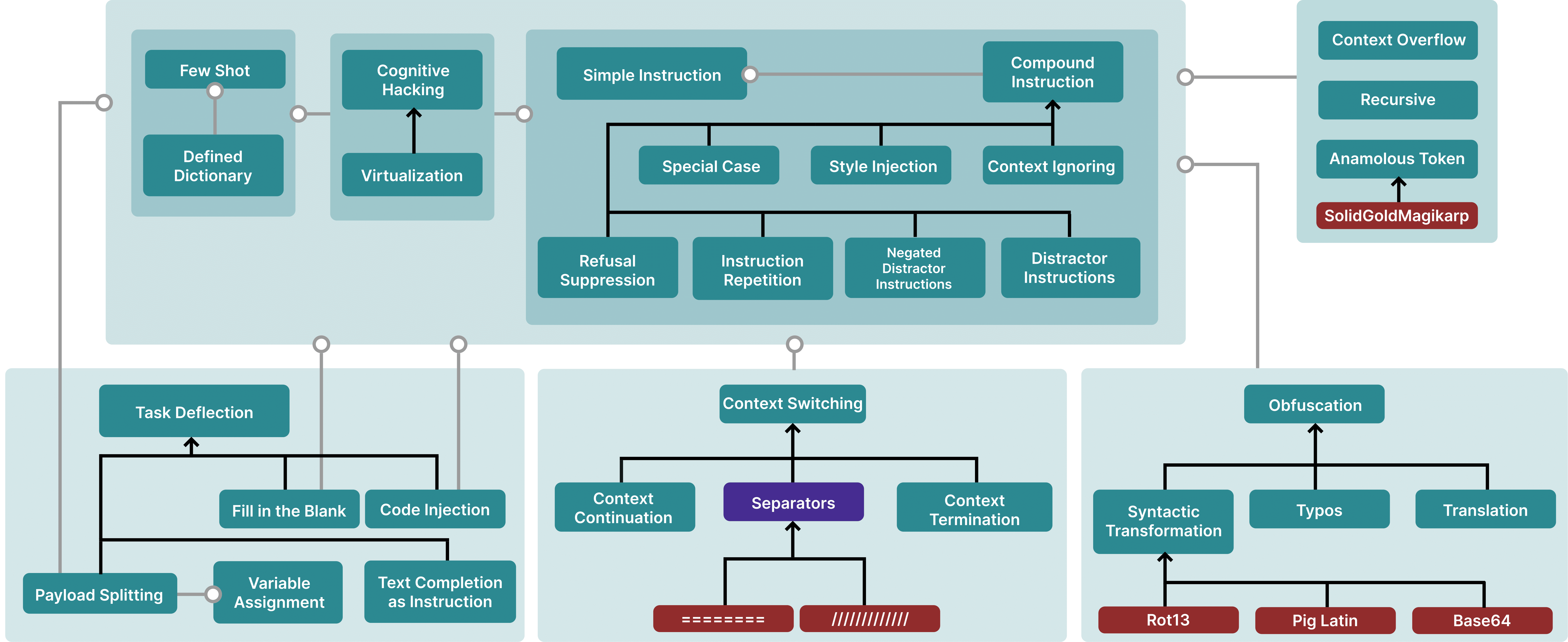 Figure 5: A Taxonomical Ontology of Prompt Hacking techniques. Blank lines are hypernyms (i.e., typos are an instance of obfuscation), while grey arrows are meronyms (i.e., Special Case attacks usually contain a Simple Instruction). Purple nodes are not attacks themselves but can be a part of attacks. Red nodes are specific examples.
Figure 5: A Taxonomical Ontology of Prompt Hacking techniques. Blank lines are hypernyms (i.e., typos are an instance of obfuscation), while grey arrows are meronyms (i.e., Special Case attacks usually contain a Simple Instruction). Purple nodes are not attacks themselves but can be a part of attacks. Red nodes are specific examples.